Microsoft Digital Defense Report 2024
Oct 23, 2024 | Jindřich Zechmeister
Microsoft is one of the largest providers of cloud and online services in the world. In addition to Azure, it is also a major provider of email services, offered as part of Microsoft 365 as well as for free. This gives Microsoft access to a vast dataset of operational data. The Microsoft Digital Defense Report 2024 provides a relevant characterization of the current state of the internet and offers insights into the risks we all face. Let’s take a look at the most interesting findings.
Most Vulnerable Sectors
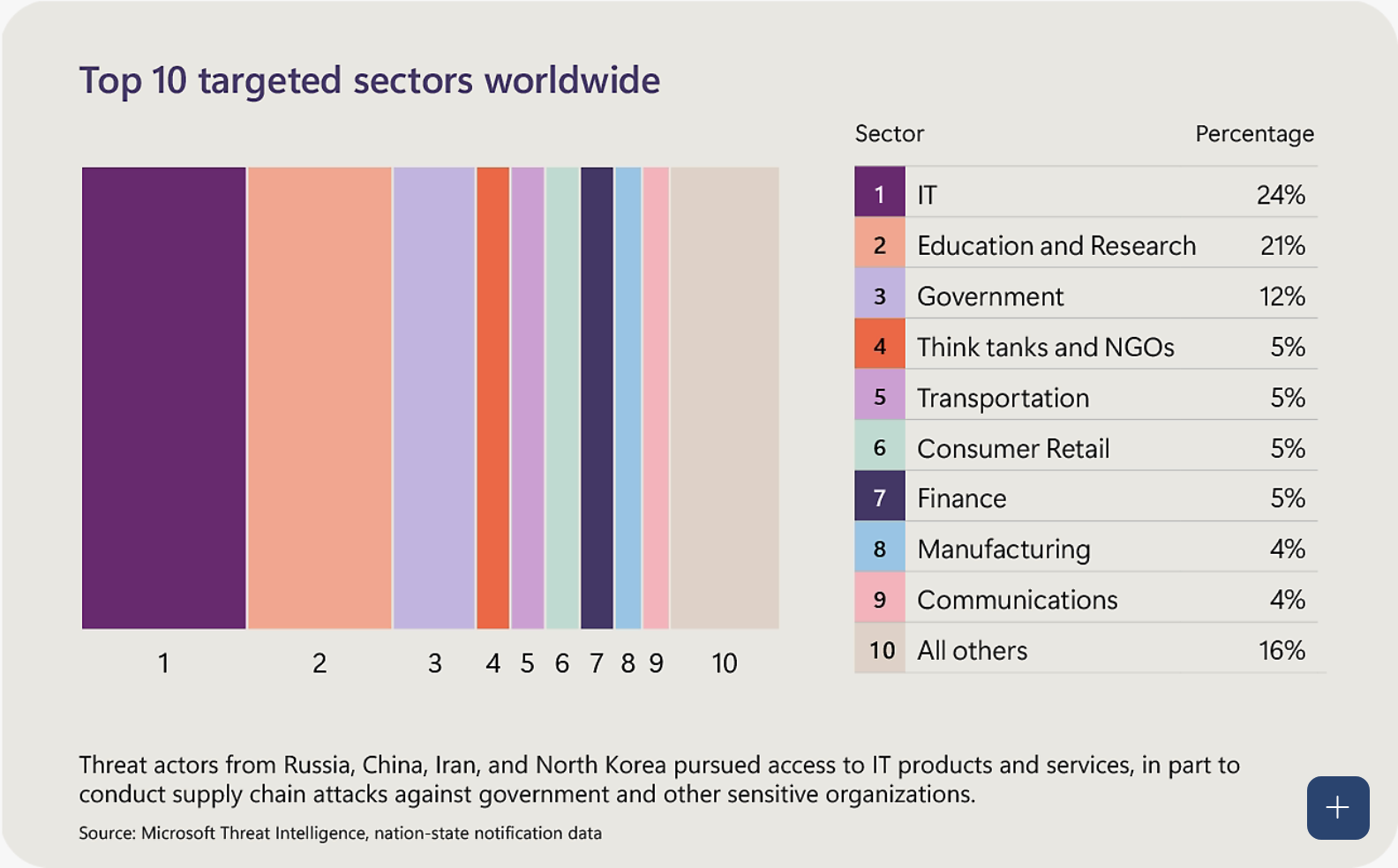
The report outlines the 10 most frequently targeted sectors worldwide. They provide insight into the key areas of attackers' interests. Let's take a look at the most at-risk areas.
The most threatened sector is the IT sector with 24%. IT products and services are logically targeted because IT infrastructure plays a fundamental role in all sectors and contains key information and access points. Cyber attackers focus on IT to disrupt services or gain access to other sensitive information.
Education and research come in second place with 21%. This might be due to the high amount of sensitive data, including research and academic information, which can be very valuable to state actors and other interest groups.
In third place, with 12%, are governmental organizations. They are often targeted due to the information they hold, which can impact national security, policy, and other strategic areas.
Year-on-Year Threat Increase
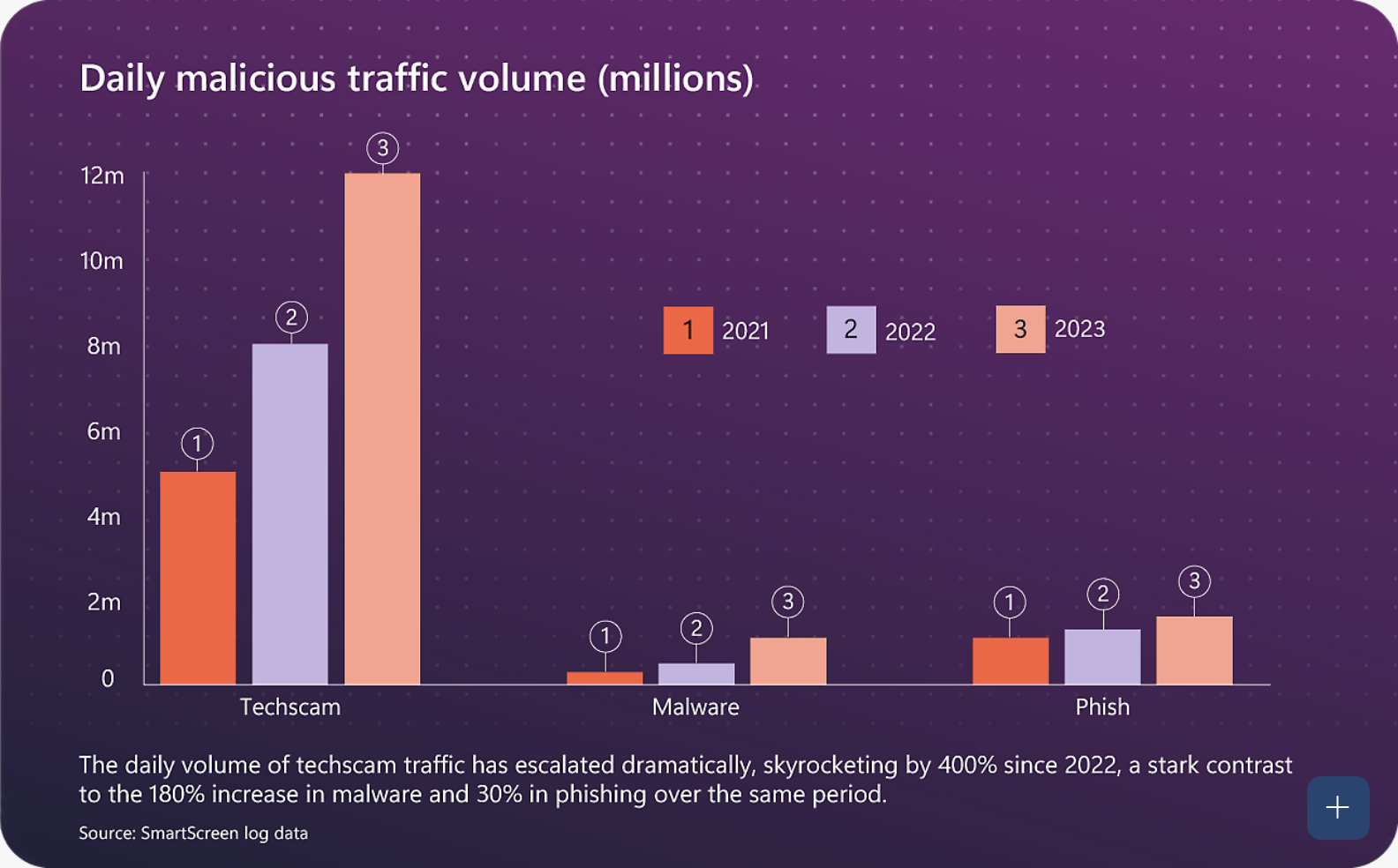
In a recent two-part article How to Avoid Internet Scams and Not Become a Victim, we alerted readers to the most common risks and recommended how to prevent them. Such a warning is entirely appropriate, as confirmed by the report. The number of scams intercepted by Microsoft has significantly increased. The following chart illustrates the daily volume of malicious traffic (in millions) from 2021-2023 for three different types of cyber attacks: techscam, malware, and phishing. This data comes from Microsoft SmartScreen logs and demonstrates a dramatic increase in cyber threats in recent years.
The area with the most dynamic growth is techscam, i.e., false emails imitating technical support communication of well-known services. Between 2021-2023 techscam increased by 400%, whereas traditional malware in the same period "only" by 180%.
Password is Still the Most Common Target
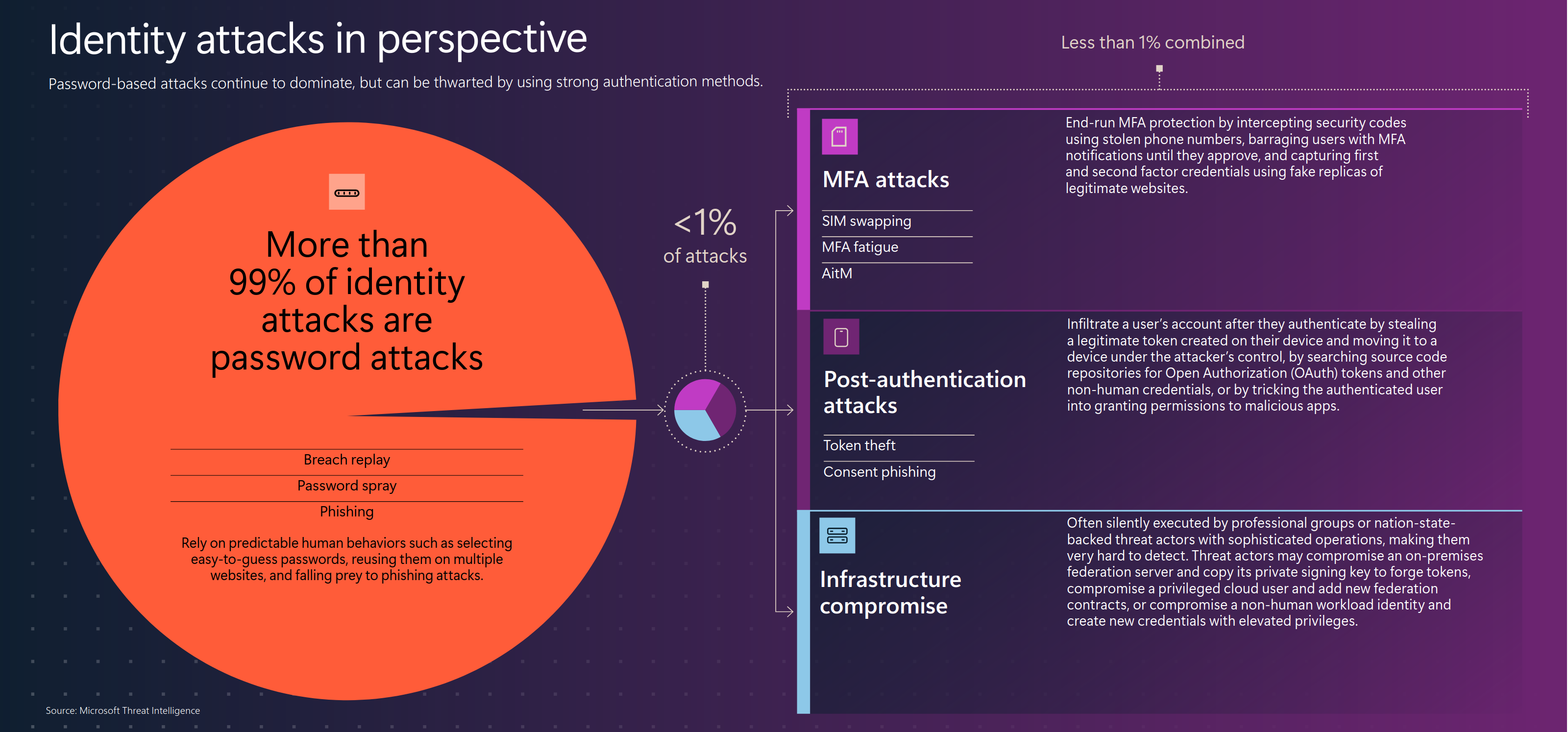
Most attacks aiming to steal someone's identity and access are still conducted on usernames and passwords - a full 99%. Microsoft blocks 7000 such attacks (password guessing attempts) per second!
We therefore recommend using multi-factor authentication (MFA). Attackers are just starting to learn how to attack MFA, and although they are making progress, it still offers good account security (the remaining one percent of attacks). Attacks in the form of so-called SIM swapping, where an attacker gets the victim's SIM from a mobile operator, are fortunately not easily realizable. An informed user knows that multi-factor authentication using SMS is no longer secure and is on the decline.
Frauds Taking on New Forms
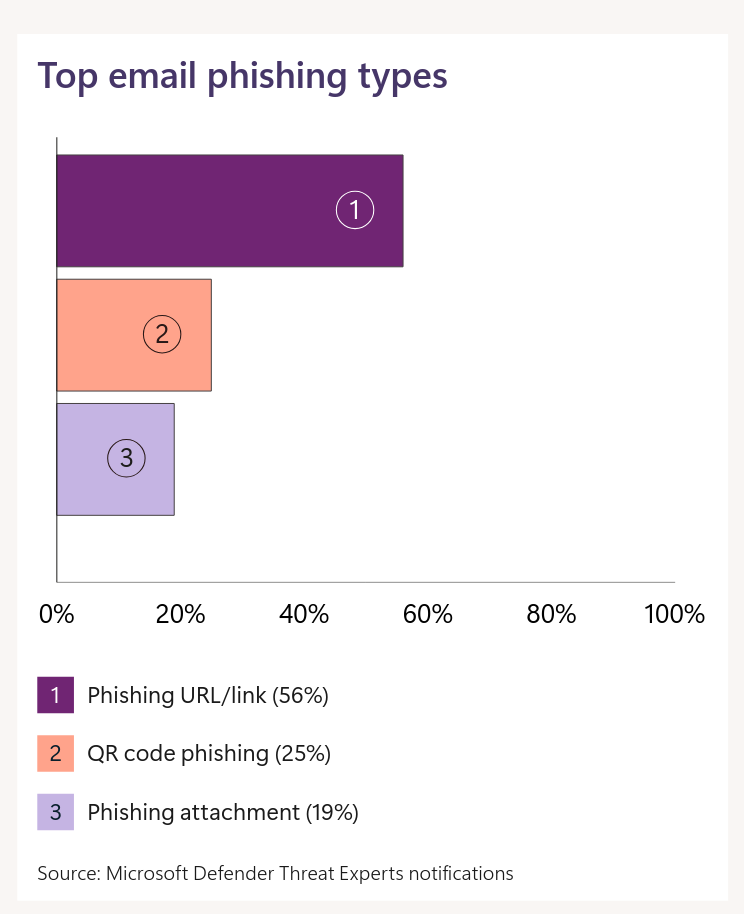
The following chart illustrates the most common types of phishing attacks via email. It displays three main methods of phishing attacks and their percentage representation.
Phishing is a constant in cybersecurity and still dominates. Attackers embed malicious links into the email body, which redirect users to fake websites where their login credentials or personal information are typically stolen. Over the past year, their number increased by 58%. The most common method is still sending fake URLs/links.
QR code phishing is on the rise and already accounts for 25%. It's a popular method for attackers to bypass security mechanisms that check email attachments and links. An image with a code easily passes through. Be cautious with unfamiliar QR codes; don't scan them and use them. If you do use them, check what they contain. Check if they're not covered over and don't look strange. These attacks are already happening at gas stations and are referred to as quishing.
The final method of phishing distribution is sending malicious attachments in emails. These attachments may contain malware or be designed to steal sensitive data. This method represents 19% of phishing attacks.
Artificial Intelligence Enters the Game
AI helps attackers create Deepfakes, which are difficult to detect. They most often appear as fake photos, but due to the rise of AI, it's no obstacle for attackers to make authentically-looking fake videos. Such cases of service advertising using fake videos of politicians are known from the Czech Republic, e.g., the deep-fake case of Andrej Babiš and Petr Pavel.
Microsoft offers an online service to help you verify the authenticity of a given medium. It's called Microsoft Content Integrity, and you can upload suspicious media to it. The application will tell you whether it's AI-generated content or if it has been altered.
Techscam, which we already mentioned at the beginning of the article, grew 12 times year-on-year. Attackers primarily target obtaining cloud service accounts because it gives them the most assets and can compromise entire servers. Simply put, it pays off the most for them.
Phishing in Cloud Services
Even services like Microsoft 365, which are fully cloud-based and monitored, aren't spared from fraud. Attackers try to exploit every means the platform offers and are quite successful at running short-term fraudulent campaigns.
Under the onmicrosoft.com domain, fake tenants appear that look credible and most often pose as tech support. They send victims malicious files, ask for their login details, or try to infect them using remote access.
Final Advice
The Microsoft Digital Defense Report 2024 doesn't give us much positivity because internet fraud is still growing. Fortunately, we have increasingly better tools to handle them, including artificial intelligence (AI). Large companies are incorporating it into their security operations, racing with attackers over who will have the upper hand at any moment.
Remember this important rule: be cautious on the internet and trust no one. Be particularly wary of when someone asks you for something, wants to change your password, or offers something for free. These are typical forms of fraud.
TLS certificate specialist
Certificated Sales Expert Plus
e-mail: jindrich.zechmeister(at)zoner.com
