How to Avoid Online Scams and Not Become a Victim - Part 2
Sep 24, 2024 | Jindřich Zechmeister
On the internet, the risk of scams awaits you at every turn, and you can't trust anyone or anything. Money is always the top priority, which is why attackers want it too. Our article will help you identify and understand these threats, navigate through them, and show you how to stay safe in the online environment.
```htmlHow to Protect Yourself from Internet Fraud
In the first part of the article, you were introduced to the most common forms of internet fraud. Now let's look at how to effectively defend against them.
It's good to adopt some basic habits. Do not click directly on links that are sent to you, but visit internet banking and other services directly. Most harmful links are still sent via emails. If you want to use a link, check where it points. In HTML, it is very easy to point a link to a different domain than what is written in the link.
Email has been used for over 50 years, and this technology did not originally account for spam and falsifying sender identity. It is extraordinarily trivial to spoof a sender's name and address in an email; what you write is what you have. In response to fraud, a number of technologies have been developed to protect us from these frauds. They are quite widespread now, but we still do not recommend opening links in emails from unknown senders. And we certainly do not recommend opening messages marked as SPAM.
Be cautious with unsolicited messages, especially if they contain links. Email remains the biggest carrier of phishing attacks and will likely be for a long time. Right behind it are social networks. Consider all links received via chat on social networks as at least suspicious.
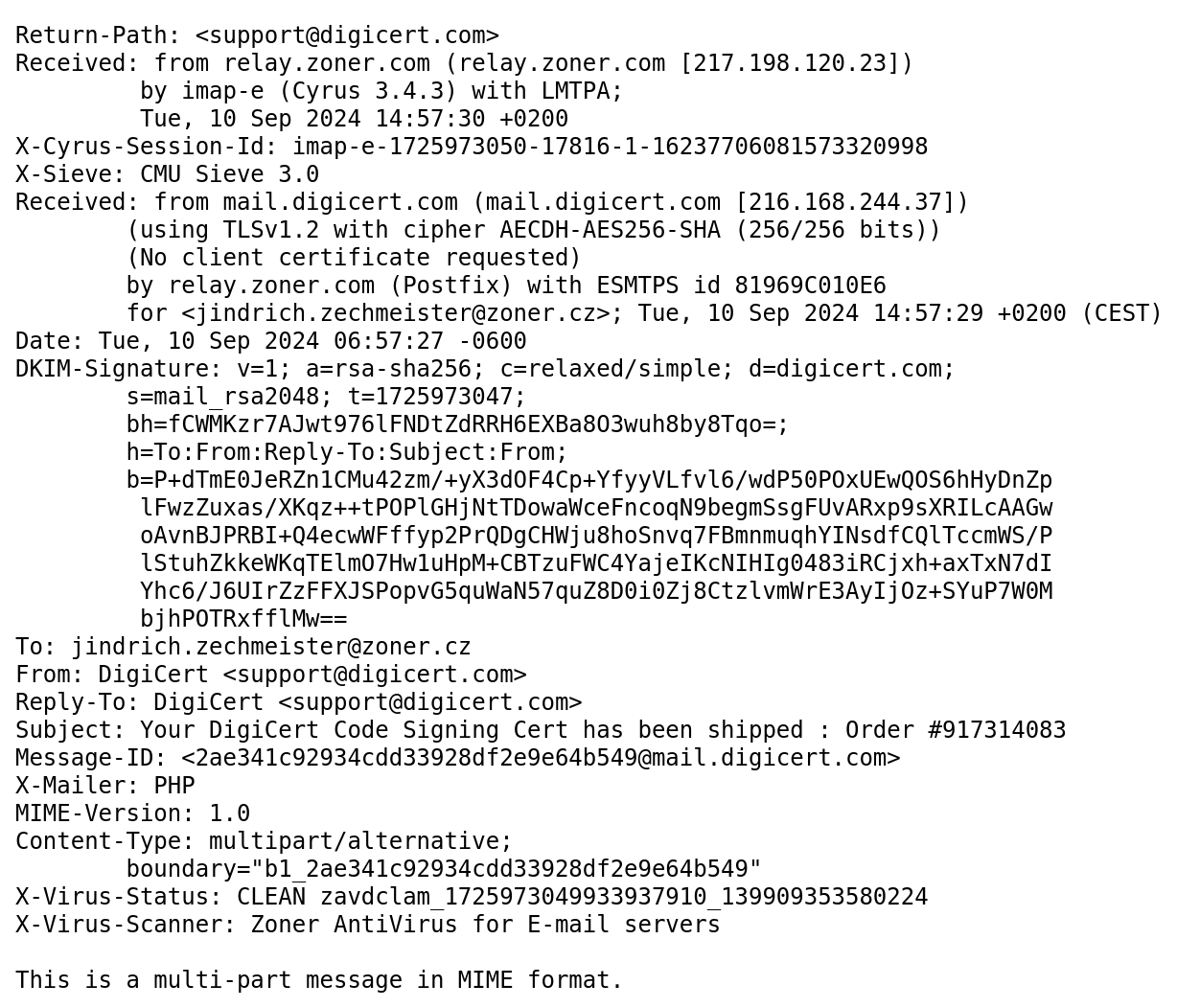
For every received email, you can view the so-called header, i.e., complete technical information that includes the actual sender and the entire route of the message on the internet. A regular user cannot understand the email header, and although there are tools for its analysis (see the links section), we recommend choosing a quality mail provider that provides this protection automatically for you. For example, CZECHIA.COM mail services use Antispam, Antivirus, and Antimalware. By combining SPF, DKIM, and DMARC technologies, they ensure that no fraudulent email reaches your inbox.
If you ever want an expert to check a suspicious email, do not forward it — it’s useless. Save it in EML format (extension .eml) and send it with the email headers.
If you want to log in somewhere, especially to your bank, always type the link into the browser manually. After completing actions, log out of sensitive systems. If in doubt, check that your bank, for example, has the certificate issued for it on that site (and not an anonymous one without any information).
In the field of shopping, frauds have been happening since the internet was the internet. Fraudsters urgently ask for payment in advance and then do not deliver the goods, or they send a brick. We recommend not falling for suspiciously advantageous offers, not using anonymous marketplaces, and always paying through a mediator (auction portals like eBay). Shop only in stores you know, because many e-shops are Chinese, the goods are delivered late or not at all, or they will quietly rob you. Do not give e-shops your credit card details; use other methods instead (see the paragraph Other Principles of Protection).
And finally, I repeat the basic rule from the beginning - do not believe in miracles. Do not believe in miraculous lottery wins, fund transfers to your account, and love over Facebook.
Use Strong Passwords and Two-factor Authentication
Strong passwords are important so that an attacker cannot easily guess or crack them. If you have a short password, an attacker can easily break it with a brute force attack by trying all possible combinations of characters and numbers and gradually increasing the length, or by trying a dictionary attack. That means they will try already known and cracked passwords as well as common words.
So, we know that the password should not be short and should not be a common word. The password should contain numbers and special characters to make it more complex. However, users make a big mistake by adding numbers and special characters at the end of the password, where they are useless.
It is critical not to use names, such as those of family members. Let's give an example of how password selection often occurs. Mr. Smith wants to remember his password well, so he chooses his wife's first name as the base. He thinks it is a good idea; it is not a common word, and he can remember it well. The password "Jane" is short on its own, so he needs to supplement it with something. To still remember the password well, he adds his wife's birth year at the end, resulting in the password "jane85" or the longer version "jane1985". This password has acceptable 8 characters, and some services may accept it. However, Mr. Smith encounters that many services refuse to accept the password because it lacks a capital letter and special character. How will he cope?
Another version of the password "Jane1985!" arises, containing a capital letter and a special character. This password has a better chance of being accepted by services. And if he needs to change or extend the password, he simply adds another special character at the end.
Mr. Smith showed us the worst possible procedure that can be chosen and unfortunately is still widespread. For an attacker targeting him, it will not be a problem to find out his wife's name. And it will surely not be a problem to find out her birth year. Then the attacker is only one special character away from cracking the password, but he knows it will probably be at the end. So, he tries a few special characters, and the password is cracked in a few seconds.
Does that sound exaggerated? Such cases are known; an attacker only needs a sufficiently strong motive (acquiring money, jealousy, blackmail, or even plain boredom). Use password generators exclusively for creating passwords, which are part of every good password manager. Many password generators are also online, such as Password Generator Plus.
Tens to hundreds of passwords that an average internet user uses cannot be remembered (and we certainly will not repeat passwords). Use password managers, so you do not make attackers' jobs easier. Tips for suitable password managers can be found on our blog, see category Password Managers.
How to Use Two-factor Authentication to Protect Your Accounts
Two-factor authentication (2FA), also known as two-step verification, involves entering a short-term code to confirm the login. This short-term confirmation code is generated in apps such as Google or Microsoft Authenticator, which are free. It typically has a validity of one minute, and without it, login is not possible.
Two-factor login has great practical advantages - even if someone else knows your login credentials, they cannot log in if they do not know the temporary code from the Authenticator. And that's exactly what you want!
The possibility to use 2FA can be found practically with all major services, whether it's Gmail, Facebook, Instagram, or Netflix. Banks have mandatory secure login using an additional factor for a long time; they most often use biometric means (fingerprint on a smartphone) for login approval.
For completeness, let me note that besides two-factor authentication, there is also multi-factor authentication (MFA). While 2FA involves exactly two factors, MFA can include more than two factors (such as the aforementioned fingerprint biometric).
Other Protection Principles
I will mention other important principles, which, although not as crucial as a good password in a password manager, must not be forgotten.
- Treat social networks as suspicious and dangerous places. Never click on links sent to you, and do not respond to unsolicited messages.
- Never share personal information online: what you tell the internet once, you will never get back. You have no control over the information. If someone asks you for personal information or a personal document, assume the worst intentions.
- Use secure payment methods: I recommend not entering the credit card number and security code anywhere, not even in a payment gateway. Today there are much faster and safer payment methods, such as Google Pay or Apple Pay. If they are not available, use PayPal. Never give payment details directly to the merchant, see the next point.
- Monitor your accounts for suspicious activities: There are dishonest merchants (e.g., the Temu case), who try to deduct money from your credit card after a certain period of the first purchase, which does not belong to them.
- Update software and antivirus: Keep your operating system on your computer and smartphone up to date, as well as the latest version of your browser and antivirus software (if you have Windows 10 and later, the antivirus is already included). Beware of antiviruses, they can also be a source of infection, and there are dozens of fraudulent antiviruses. In the best-case scenario, they will unnecessarily drain your money.
- If you need to verify a program and did not get it from a trusted source, do not hesitate to use VirusTotal (see links) and have it scanned.
If you have read this far, thank you for your attention. It is evident that you are interested in your online security, and I can assure you that if you keep the above advice in mind, you will significantly reduce the risks of fraud and possible trauma.
Artificial Intelligence Brings a Revolution in Fraud
We are now undergoing an IT and industrial revolution that will undoubtedly be significant for humanity. AI (artificial intelligence) can help us with various tasks, save us time, create art, and other previously unimaginable outputs. It is logical that from the very beginning, attackers are also exploiting it.
Artificial intelligence can help write more trustworthy and well-translated fraudulent emails. It is not a problem for it to create a video with a particular person or perfectly imitate their voice. You only need some samples that serve to train the AI. Today, AI can create videos of fictional events, generate speeches of politicians where you put words into their mouths, and they never said.
Soon, unfortunately, we will also experience fake calls in our country, when our boss will call us and want, for example, to transfer money to his account. And due to AI, you will not distinguish him from the original. Defending against this is a challenge that awaits us all; and it certainly will not be as simple as detecting a fake email sender.
Be on your guard, because frauds will take on unknown and previously unimaginable forms. As the classic saying goes - "trust no one". I will add: If you are communicating via the internet or phone.
Useful Links:
- Have I Been Pwned - A free online service that allows users to find out whether their email addresses or passwords have been compromised in data breaches. Users enter their email address, and if it was part of a security breach, HIBP displays details about which database was compromised. The service also offers the ability to set up alerts if the entered email becomes part of future breaches. It is managed by cybersecurity expert Troy Hunt and provides valuable information about data protection.
- Mozilla Monitor - This service from Mozilla helps you determine whether your email account has been affected by a data breach. Firefox Monitor also informs you about the latest data breaches and provides useful information on how to protect your personal information.
- DeHashed - This service allows users to search an extensive database that contains information on data breaches. DeHashed offers advanced search options that can include names, usernames, IP addresses, and more.
- Zoner AntiVirus Online - An online tool for verifying files. You upload a suspicious file to the tool, and it checks whether it is "clean" or not. Zoner Antivirus uses its own heuristics and is the best at detecting new vulnerabilities that others do not yet know (so-called "Zero-day" threats).
- VirusTotal - An online tool for verifying files and links. You upload a suspicious file to VirusTotal, and it will check it with dozens of antiviruses. You will get an idea of whether the file is "clean" or not.
- Google Admin Tools - Messageheader - This tool will make it easier to analyze email headers and confirm if the message has DKIM and DMARC.
- Email Header Analyzer - A tool for analyzing email headers for advanced users and administrators.
TLS certificate specialist
Certificated Sales Expert Plus
e-mail: jindrich.zechmeister(at)zoner.com
