How to Avoid Online Scams and Not Become a Victim - Part 1
Sep 17, 2024 | Jindřich Zechmeister
On the internet, the risk of scams awaits you at every turn, and you can't trust anyone or anything. Money is always the top priority, which is why attackers want it too. Our article will help you identify and understand these threats, navigate through them, and show you how to stay safe in the online environment.
Most Common Types of Internet Scams
On the internet, you are most at risk from two types of threats - phishing and social media scams. Let's take a closer look at them.
Phishing involves deception aimed at obtaining sensitive information from the victim. It has many forms but one common goal - to obtain your login details or money. It is often accompanied by extortion, as this provides a steady income for the attacker.
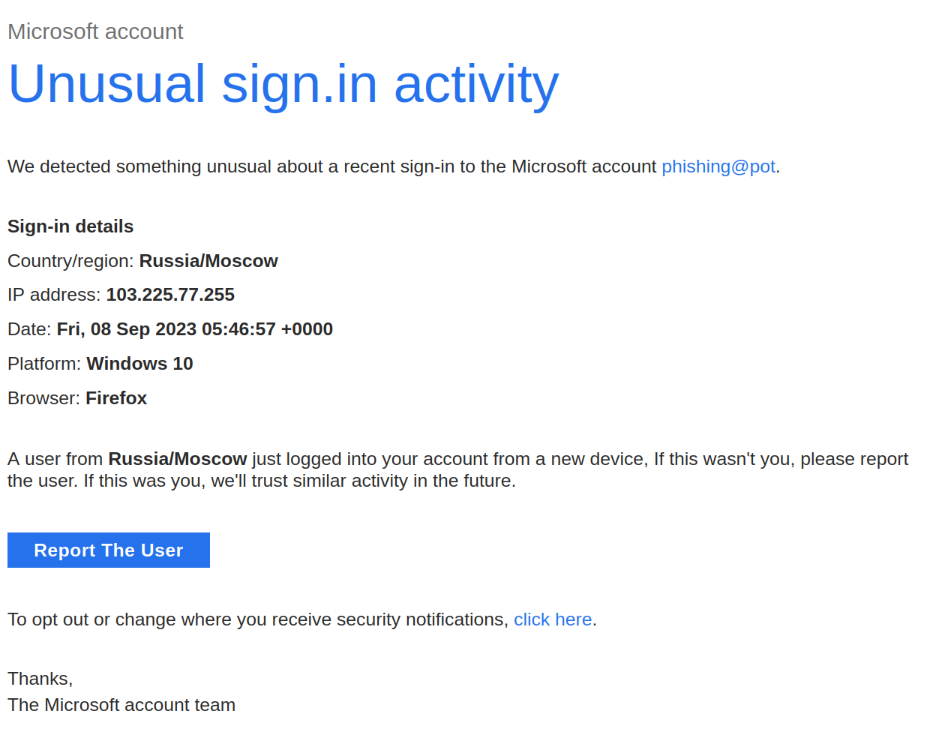
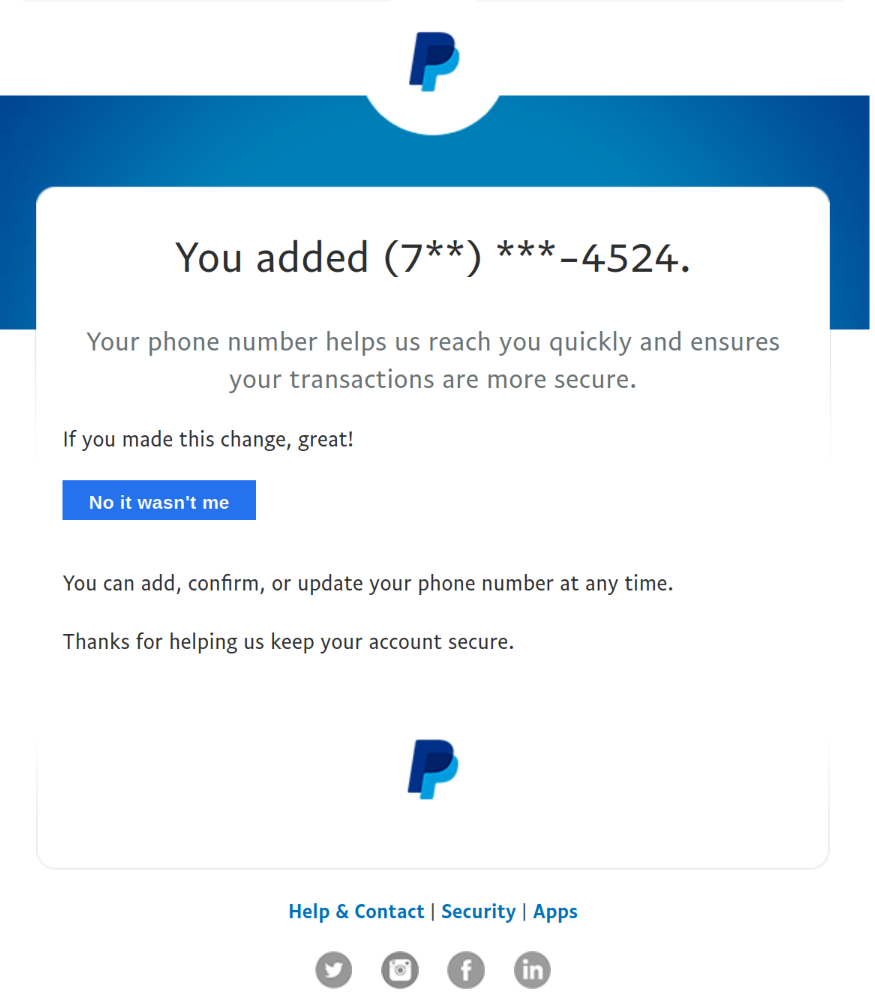
The form of phishing is sophisticated to make the victim believe it. Attackers create fake versions of login pages that are indistinguishable from the original. Once you enter your details, you can assume they are compromised. Links to fraudulent websites are spread via fake emails, messages, or links that mimic well-known institutions and services. It's easy to fall for this and accidentally click the link, as it's often when you are expecting a delivery. If something seems strange or suspicious when logging in, it's better to leave.
Scams on social media and dating sites consist of fake profiles, "romance scams," or fake competitions. The goal is mostly to gain the trust of the other party and then take their money. Do not click on links received in chats, especially from unknown contacts.
Apart from the aforementioned risks, here are some other common scam methods:
- Fake online stores: These are suspicious e-shops offering unrealistically low prices but never deliver the ordered goods. Ads on marketplaces often ask for money upfront and deliver nothing.
- Fraudulent job offers: Work-from-home offers promising unrealistically high earnings but aim to misuse your personal data. These should be easy to spot.
- Ransomware and extortion: An attacker encrypts your data and demands a ransom for decryption; or uses sextortion scams to extort you.
- Malware distribution: Attackers offer malicious software disguised as legitimate files or applications. Often, malware is disguised as antivirus software or a necessary tool.
How to Recognize Scammers and Fraudulent Activities
The primary defense against these risks is common sense. Just think about how likely it is that you won a (foreign) lottery, or how unrealistic it is that someone from Nigeria wants to send you millions of dollars. It's also unlikely that an anonymous Facebook contact is your true love. On the internet, it's essential to maintain a critical perspective and a healthy dose of skepticism, then you can fend off many threats. Miraculous get-rich-quick schemes, rejuvenation promises, expensive gifts for free... all are just different forms of scams.
"Remember the golden rule - be suspicious of anyone who supposedly wants to do good by you (or offers you something for free)."
Fraudulent messages often contain a high sense of urgency, putting you under stress and stopping you from thinking and making decisions calmly. Be cautious in these situations and always verify the source. Similar tactics include offers expiring in a few minutes and emails claiming your account is expiring, urging you to click something immediately, renew something, or even change your password. This is typical phishing. Always visit the login pages of services by typing their address directly; do not click any links. Any link leading to a login page is suspicious.
The most coercive and personal is the so-called Sextortion scam. An attacker sends you an email seemingly from your email address, claiming to have gained access to your computer or email. In reality, it is just a forged sender's name, something DMARC (a task for the email provider) should solve. The content of Sextortion messages announces that the attacker recorded you while masturbating and intends to blackmail you by threatening to release this material unless you pay. This is, of course, a lie and an attempt to start extorting you. Once you respond and pay something, the extortion will truly begin and never stop.
Another variant of attacks target organizations by infiltrating the network and encrypting the victim's data. The attacker demands payment for access to the data. Again, never pay the extortionists. Instead, seek help from IT professionals who may have tools to decrypt your data or have backups.
"If someone tries to extort you, never pay them. They will only start a relentless cycle of extortion."
There have been several waves of "execution" phishing and fake invoice waves. For companies and individuals, this was unexpected, and the connection with an executor was provocative enough to grab attention. Fake invoices rely on the assumption that no one will check them and will just pay them automatically. QR codes associated with payments and invoices are also a popular attack vector. Simply replacing the QR code on an invoice with a fake one sends money to the attacker's account. Therefore, it is wise to send invoices as electronically signed (PDF) - the signature ensures their immutability.
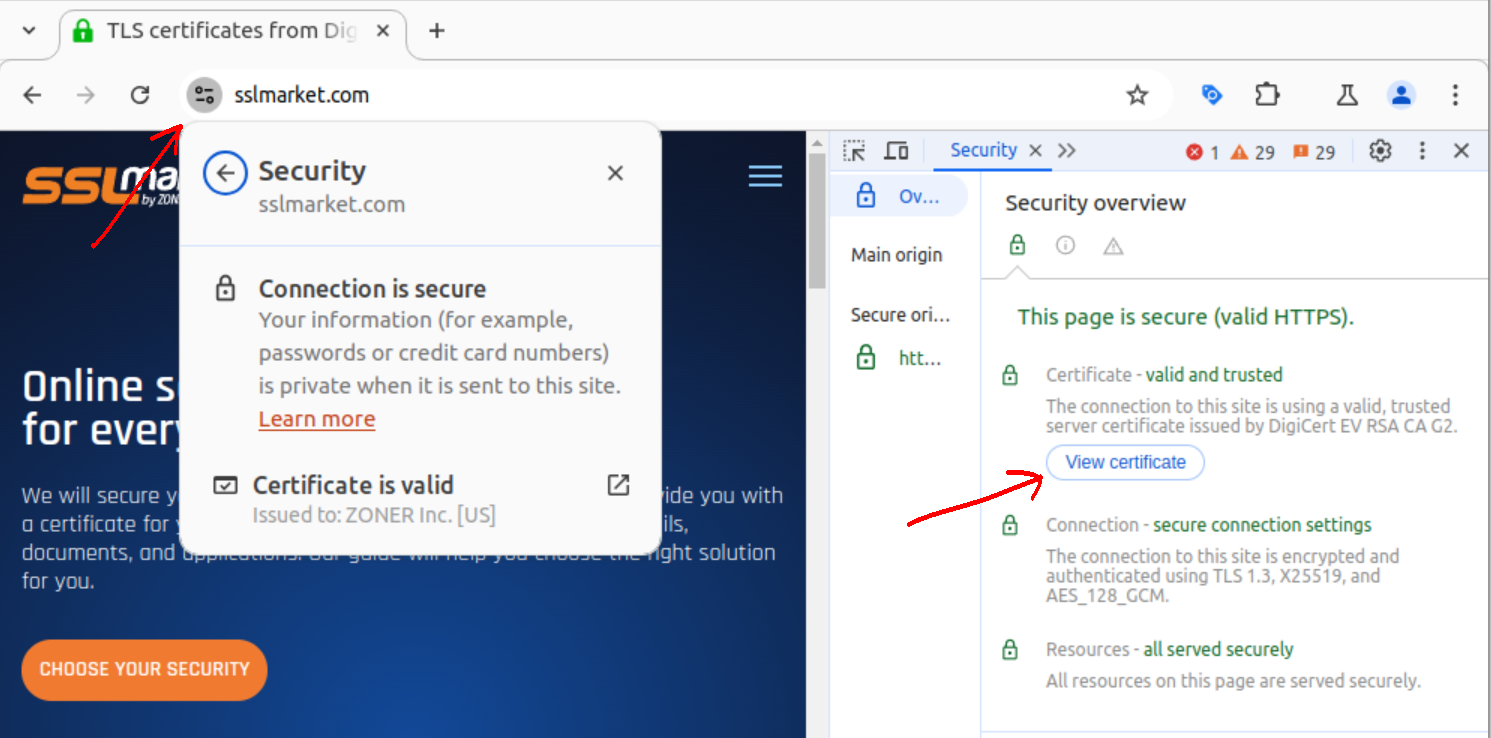
There are many fraudulent websites on the internet designed to steal login credentials, as mentioned earlier. Never click on links in unsolicited or suspicious messages. If you are on a bank or service login page, it is recommended to pay attention to the domain in the address bar and check the TLS certificate used by the website. Every reputable institution uses a certificate with verified details that you can view. Attackers, on the other hand, use anonymous certificates because they can't get others. You can find certificate details in the browser console by pressing F12 (Security tab).
In the second part of the article, we will focus on practical ways to protect yourself from internet scams.
TLS certificate specialist
Certificated Sales Expert Plus
e-mail: jindrich.zechmeister(at)zoner.com
